The rise of Internet as the main – and often only – communication channel between computer networks in the past 20 years has exponentially increased the vulnerability of computer systems to malicious attacks coming from outside the walls of an organization. Until a few years ago, the major target of cyber-criminals was information systems. Misappropriation or destruction of confidential information, which per se is a risk that predates the advent of computers, has become much more serious today as nearly all of an organization’s data are stored inside information systems that can potentially be accessed from the outside.
While loss of data can be extremely harmful to an organization in financial terms, an attack of this kind rarely affects the safety of people involved in it. But in the past 10 years, malicious attacks to computer system have reached new, potentially catastrophic, levels with the emergence of Cyber-Attacks targeting computer systems controlling all sorts of civil, industrial, and military processes.
According to NATO’s Tallin Manual, a Cyber-Attack is “a cyber operation, whether offensive or defensive, that is reasonably expected to cause injury or death to persons or damage or destruction to objects.” With computer systems controlling power grids, chemical plants, telecommunication infrastructures, and even weapon systems, it is not difficult to understand how any disruption can have far-reaching implications that can, in turn, result in injury or death of people involved.
 To get a better insight into all the implications connected to cyber-security we contacted Ram Levi, Founder and CEO of Konfidas Ltd. – an Israel based cyber-security strategy solutions startup specializing in solutions for the financial, insurance, and space sector.
To get a better insight into all the implications connected to cyber-security we contacted Ram Levi, Founder and CEO of Konfidas Ltd. – an Israel based cyber-security strategy solutions startup specializing in solutions for the financial, insurance, and space sector.
Untrustworthy Systems
Levi starts by clarifying the approach of his company to cyber security “Cyber-Attacks are attacks that cause the adversary’s computer systems to become untrustworthy. Konfidas is based on a unique approach, preparing companies for cyber threats by understanding an attacker’s mindset.”
“Cyber-Attacks are, in a way, about reverse engineering a system to understand how it operates and how to cause to do what it was not always planned to do,” states Levi. As an example, a nuclear power plant is kept in a safe state by the procedures according to which it is operated. When an attacker breaks into its control system, he can force it to perform unsafe operations that can have all sorts of catastrophic consequences. “We can find numerous examples of such attacks,” says Levi. “The most well-known one is perhaps Stuxnet, which was the cyber-attack to the Iranian centrifuges discovered in 2010. In this attack, the attackers caused physical damage to the centrifuges by attacking their controllers and computers used for command and control, with resulting physical damage to the centrifuges and thus to the enrichment process. Another example happened in 2001 where a former employee hacked into the Maroochy Shire sewage system in Queensland Australia and caused millions of liters of raw sewage to spill out into local parks and rivers.”
An attack requires four elements: the possibility to access a system, a vulnerability to exploit, a payload – a malicious logic to be executed within the victim’s system to cause damage once executed, and command and control to tell it what to do. “One scenario could be a distributed denial of service attack (DDoS),” Levi explains. “In this scenario the attacker is denying the ability of the system to provide services to its legitimate user by choking the network or overloading the server with requests to diminish the limited resources of the server. Another attack could grant access to sensitive computers controlling industrial processes to manipulate the outcome of the process – such as changing the speed of an electricity-generating turbine and at the same time showing ‘normal’ operation status to the control technicians. Such attacks are hard to execute but also extremely hard to deal with – high complexity, high gain attacks.”
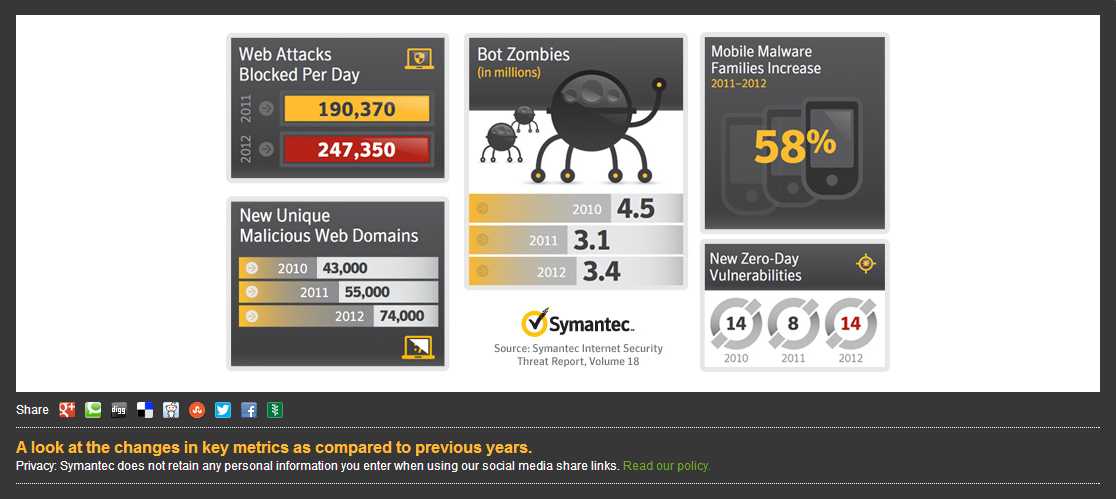
With computer systems permanently connected to the Internet, the ability to perform an attack depends on the knowledge of a particular vulnerability. “A vulnerability may be due to design errors in coding of software or hardware” Levi explains. “There are also backdoors which can be planned or covertly inserted in the software/hardware development process.” The most valuable resource for a cyber criminal is what is called Zero Day vulnerability, a vulnerability that has not been publicly disclosed. “Those vulnerabilities are unknown to the general public or the software or hardware developers and therefore can be exploited by an attacker,” says Levi, adding that these are literally “a ‘free-pass’ to the organizations’ IT systems that can be used sometimes for over a year, according to research done by Symantec.”
Space Systems Vulnerability
Space systems, which in turn are composed of a network of ground stations and spacecrafts using satellite communication for specific purposes, are themselves potentially subject to these same vulnerabilities. “The components of space systems are computers, network components, or components controlled by computers, like uplink antenna motors,” Levi explains. “None of them would successfully work without the computers that are controlling them, including the onboard computer in the satellite. Computers control everything the space systems do and they are vulnerable to Cyber-Attack on them.”

There’s no need to attack a satellite when you can attack it’s ground-side services instead (Credits: Looking Glass).
The worst-case scenario in space Cyber-Attack would be if someone managed to hijack a satellite after penetrating the command and control computer of the satellite. “This scenario is an operator’s nightmare, and we can assume that all measures are being taken to safeguard against such threats,” says Levi. “However, if we are looking at the satellite service – the service the satellite provides – one can attack the service rather than the satellite itself.” This could mean, for example attacking communication links between satellite ground stations and the broadcasting source instead of jamming the signal. This way, the satellite system would be working perfectly, but its service would be denied. Levi explains that from the point of view of an attacker, this brings the same result but without the strategic risk of directly attacking or jamming a satellite system.
Levi quotes Gen. William Shelton, commander of US Air Force Space Command: “There’s not an operation conducted anywhere at any level that is not somehow dependent on space and cyberspace,” adding that this dependency could be used to attack space assets from cyberspace. “From a cyberspace perspective, it’s irrelevant how high above the ground a computer is positioned.”
But attacking the services a satellite provides is not the only approach to compromise a satellite system. “Space systems are computer systems; this requires a new approach to better safeguard satellite systems from attacks,” Levi says. “Such protection should include not only focusing on the protection of the satellite itself, but thinking about broader protection.” A broader protection would need to take into account the supporting systems that enable the satellite to provide service, like communication, electricity, water supply, sewage and so on. “Such protection is much more complex, but possible. Considerations to this sort of protection should include re-analysis of the systems and the dependence of the satellite systems computer systems and their sensitivity to Cyber-Attacks.”
A New Approach to Defense
From the attacker’s point of view, the major advantage of performing an attack from Cyber Space instead of directly is the Attribution Problem, or the difficulty in identifying the source of an Cyber-Attack. “Internet was built in the form of a network of networks, with no central management,” Levi explains. The communication is based on Packet Switching, an approach that consists of dividing a message in packages that follows independent routes to the receiver. This approach created a a system that is almost immune to malfunction of one or more nodes. “Cyberspace is based on these and other principles,” says Levi. “Satellite systems are also based on those principles. Now, since an attacker can connect to the internet from virtually anywhere, the attack can be executed from anywhere. All you need is a laptop and an internet connection.”
The situation is scary, but fortunately not hopeless. “The good news is that it requires a lot of knowledge and skill to successfully execute attacks,” Levi says. “Although attackers have many possibilities to attack and many vulnerabilities to exploit, defense methods, tools and technologies are advancing as well.”
 According to Levi, this problem can be solved by shifting to a new paradigm that could increase the cost on the attacker, compromising his will or ability to Cyber-Attack satellite systems. “The systems we use are mostly unchanging and not very dynamic in their configuration so, currently, attackers have an advantage in exploiting systems,” Levi explains. “Once a vulnerability is found – and a zero-day vulnerability in particular – there is a vulnerability window – the time the attacker needs to penetrate the system and tailor the malicious payload to the victim’s system. We can increase the cost on the attacker by making the systems much more complex and dynamic so that the he would have to pay a higher price in resources for attacking a system. Such a price could be more network intelligence, difficult and costly payload development, complex command and control architecture, risk of being exposed, and even increased uncertainty that the attack will result in higher attention given to the attacking system.”
According to Levi, this problem can be solved by shifting to a new paradigm that could increase the cost on the attacker, compromising his will or ability to Cyber-Attack satellite systems. “The systems we use are mostly unchanging and not very dynamic in their configuration so, currently, attackers have an advantage in exploiting systems,” Levi explains. “Once a vulnerability is found – and a zero-day vulnerability in particular – there is a vulnerability window – the time the attacker needs to penetrate the system and tailor the malicious payload to the victim’s system. We can increase the cost on the attacker by making the systems much more complex and dynamic so that the he would have to pay a higher price in resources for attacking a system. Such a price could be more network intelligence, difficult and costly payload development, complex command and control architecture, risk of being exposed, and even increased uncertainty that the attack will result in higher attention given to the attacking system.”
A possible approach, called “Moving Target,” is suggested by The White House report Trustworthy Cyberspace: Strategic Plan for the Federal Cybersecurity Research and Development Program (2011). “This approach, currently under research, will enable us to ‘create, analyze, evaluate, and deploy mechanisms and strategies that are diverse and that continually shift and change over time to increase complexity and cost for attackers, limit the exposure of vulnerabilities and opportunities for attack, and increase system resiliency.’ It can be seen as a way to increase complexity in a simple way.
 Ram Levi is the Founder and CEO of Konfidas Ltd. – a cybersecurity strategy solutions startup. He is also the cybersecurity advisor to the National Research and Development Council, Ministry of Science and Technology and Space, and senior researcher at the Yuval Ne’eman Workshop for Science, Technology and Security, Tel Aviv University.
Ram Levi is the Founder and CEO of Konfidas Ltd. – a cybersecurity strategy solutions startup. He is also the cybersecurity advisor to the National Research and Development Council, Ministry of Science and Technology and Space, and senior researcher at the Yuval Ne’eman Workshop for Science, Technology and Security, Tel Aviv University.
In 2011 he served as Secretary of the Prime Minister’s National Cyber Initiative Task Force that spearheaded the government resolution on establishing the National Cyber Directorate. In 2010 he I co-authored the national civilian space policy as part of the President of Israel’s committee on the Israeli National Space Policy.
Contact & Speaking requests: info@konfidas.com

























![A trajectory analysis that used a computational fluid dynamics approach to determine the likely position and velocity histories of the foam (Credits: NASA Ref [1] p61).](http://www.spacesafetymagazine.com/wp-content/uploads/2014/05/fluid-dynamics-trajectory-analysis-50x50.jpg)



Leave a Reply